Protect your confidential online meetings
Your employees exchange sensitive information during online meetings.
How can you ensure that these communications are not leaked?
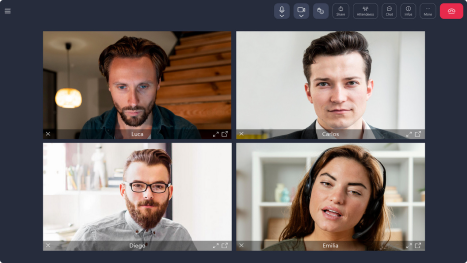
Guaranteeing the protection of your communications
Tixeo’s secure video conferencing offers the highest level of security for your confidential online meetings, regardless of the number of participants.


Tixeo, videoconferencing technology labeled by the French Cybersecurity Agency (ANSSI)
Since 2017, the French government, via the Agence nationale de la sécurité des systèmes d’informations (ANSSI), has been recommending the use of Tixeo for organisations in critical sectors.
Your secret, our protection

Your Executive Committee meets remotely
The members of your executive committee need strong security guarantees to ensure that their exchanges and file sharing cannot be intercepted by malicious parties.

You are conducting a financial audit via videoconference
A decisive moment in the life of a company, the financial audit can take place remotely, provided that it is perfectly secure. Information relating to the organisation’s economic activity must not be communicated via any video collaboration tool.
Benefits of Tixeo secure videoconferencing

End-to-end multi-point encryption
Communicate securely thanks to Tixeo’s end-to-end encryption technology. All audio, video and data communication flows are end-to-end encrypted, even those passing through the server, regardless of the number of participants.

Partitioning of meetings
To avoid data leaks, each Tixeo online meeting is executed in a separate and ephemeral process: as soon as they are over, all the information exchanged disappears and cannot be retrieved.

Rights and access management
Access to a Tixeo videoconference is secured by default. Thanks to the virtual waiting room, the organizer verifies the identity of a participant before letting him access the online meeting. At any time, they can also remove the participant from the list of participants and limit their rights in the meeting.
Cyber espionage: a growing threat
In 2023, more than 80% of state cyber attacks involved espionage.

* source : cfr.org/operations
Financial losses
Cyber espionage is a way of recovering and financially exploiting information:
- Commercial
- Strategic
- Technological…
An organisation’s intellectual property and competitive advantage can be compromised.
Destabilisation
Cyber espionage also aims to destabilise the equilibrium of an organisation or nation, by disseminating classified information or the personal data of users and citizens.

* source : cfr.org/operations
Regulatory penalties
Companies must comply with current safety regulations or face financial penalties.
In Europe, the RGPD obliges organisations to ensure the protection of personal data: in the event of a data breach resulting from a failure to comply, a fine of up to €20 million or 4% of annual turnover may be imposed.
In the near future, the NIS 2 directive will oblige many entities to strengthen their
How can you protect your online meetings from spying?
Organising an online meeting using an unsecured videoconferencing tool poses a risk of cyber espionage.
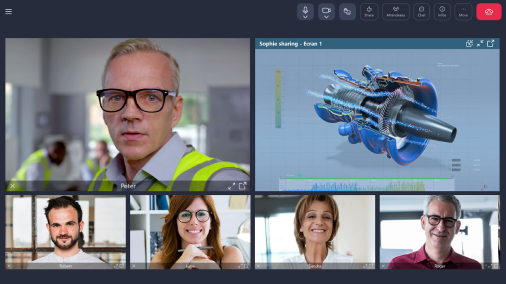

7 essential criteria to take into account:
-
The origin of the solution
-
End-to-end encryption technology
-
Deployment within the organisation
-
User rights management
-
Protection of privacy
-
Security of hosted data
-
Regulatory compliance
Rely on proprietary, sovereign technology

Why choose proprietary technology?
Tixeo, a French company, has owned its secure video conferencing technology for almost 20 years. This means that the design and specifications of its end-to-end encryption technology are the exclusive property of the company.
What’s more, its solution is designed using a Secure by design approach: security is taken into account at every stage of the design process to limit the risk of vulnerabilities.

100% RGPD compliant
As a European and sovereign solution, Tixeo is not subject to extraterritorial data protection laws and secures its users’ data in compliance with the RGPD
Everything you need to know about the processing of personal data
The benefits for our customers:


Continuous reinforcement
of safety


Reducing the risk of exploiting zero-day vulnerabilities


Meeting specific needs


Guaranteed sovereignty
Would you like to find out more?
Please fill in this form:
A Tixeo expert will contact you shortly.
Would you like to find out more?
Please fill in this form:
A Tixeo expert will contact you shortly.
Secure videoconferencing in the Cloud or On-Premise

SecNumCloud qualified sovereign hosting
With TixeoServer, the on-premise version of Tixeo, deployment in the information system is done in total control of the organization’s infrastructure, with no impact on the network security policy.

Available as an on-premise version
With TixeoServer, the on-premise version of Tixeo, deployment in the information system is done in total control of the organization’s infrastructure, with no impact on the network security policy.
Discover how Tixeo meets the specificities needs of your industry sector.
Tixeo provides a secure video conferencing technology that is used by many organisations.




